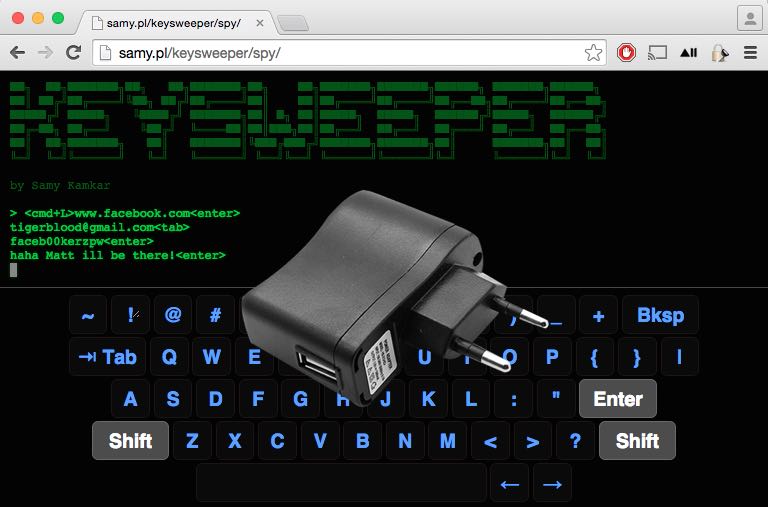
KeySweeper — You Could Be Using A Fake USB Charger That Records Everything You Type
The FBI has issued a warning for the private industry to keep an eye on a stealthy Arduino-based keylogger hidden inside a fake USB charger. Called KeySweeper, this tiny device acts as a remote keylogger that sends back the decrypted data to the attacker, exposing your sensitive information and passwords.
15 months ago, Samy Kamkar, a white hat hacker, revealed a proof-of-concept attack platform called KeySweeper. It was a stealthy Arduino-based hacking device that looked like a USB wall charger.
KeySweeper silently recorded and decrypted any keystroke from a Microsoft wireless keyboard around it. The keystrokes, it recorded, were logged online and alerts were sent when a person typed some particular words or URLs. Moreover, if unplugged, it continued to work with the help of its internal battery.
Microsoft’s keyboards use 2.4GHz wireless protocol and Samy exploited the same proprietary protocol.
Samay Kamkar open sourced the details of this hacking device whose making costs just $10-80. These are the components that are needed to make a KeySweeper device:
- Arduino/Teensy microcontroller
- NRF2401+ 2.4GHz RF Chip
- AC USB Charger
- SPI Serial Flash Chip
- 3.7 LiOn/LiPo battery
- Adafruit FONA and SIM card (optional)
Samy has also shared KeySweeper’s source code on GitHub and written about the other pieces of software on his website.
Now, the government is looking concerned about this live web monitoring tool and the FBI’s Cyber Division is warning the private industry about the same.
Here’s what the FBI has to say about KeySweeper:
If placed strategically in an office or other location where individuals might use wireless devices, a malicious cyber actor could potentially harvest personally identifiable information, intellectual property, trade secrets, passwords, or other sensitive information
The federal agency calls it dangerous as security managers may miss the leak as the data is intercepted before it reached the CPU.
This device could be used to steal a wide variety of sensitive information, varying from bank passwords to trade secrets.
So, keep an eye on any unknown USB charger lurking around in your home or company and stay safe.