Hackers are now using a sophisticated method to tap in Phone network by exploiting the SS7 protocol to steal money from
T
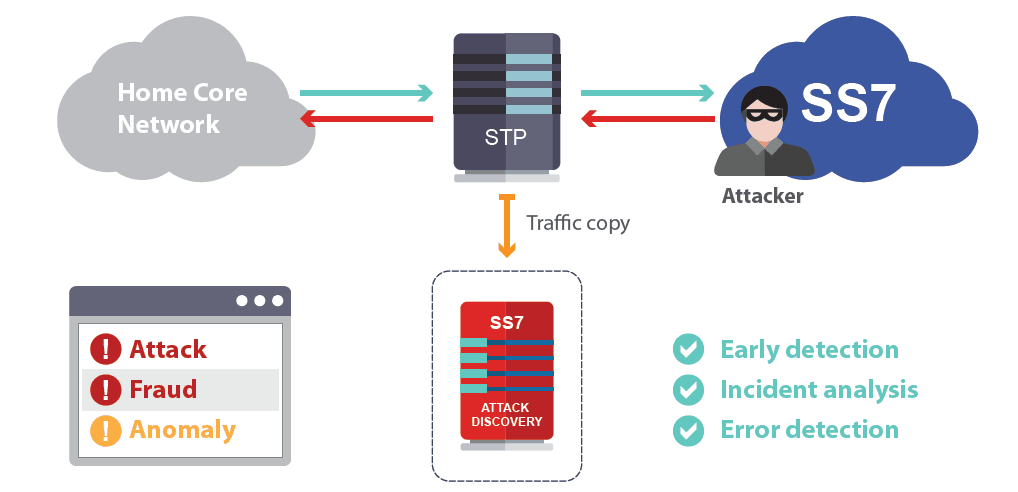
he SS7 protocol which standards for Signalling System No. 7 which internet service providers and telecom companies use to control the flow of phones calls and text messages around the world.Cybercriminals chose to perform SS7 attack using the known call existing design flaws they can perform various attacks some of which include but not limited to Data theft, text interception, location tracking, and eavesdropping.
Are your Internet Services provider (ISP) selling you out ?
Sometimes Internet service provider has to give intelligence agencies or surveillance contractors access to your data but only for legitimate purposes, because they are concern about sensitive data and privacy of there users, I know it might not sound that way but they do.
These type of attacks is most common in the hands of financially-driven cyber-criminals, which use these attack to gain access to your bank account and to potentially empty it, according to the .
They also stated that a UK’s Metro Bank has fallen victim of the SS7 attacks which cybercriminals are taking it to another level wide spreading their attacks.
You may also like: What are the different Types of Hacker’s ?
The National Cyber Security Center ( NCSC) said that “We are aware of a known telecommunications vulnerability being exploited to target bank accounts by intercepting SMS text messages used as 2-Factor Authentication (2FA).”
Why are SS7 Attacks hard to Detect ?
This may be surprising to most viewer I also admit it was surprising to me as well during my course of research in which i learned that the SS7 protocol in which we use to communicate VIA phone, text and other doesn’t carry any form of authentication in which means it doesn’t authenticate who send the request and pass it on to the other side.
In simple term, anyone gain access to the transfer of data using the SS7 protocol the system will see it as legitimate in which request can be made from a government agency, surveillance contractor or a criminal, which will all seem legit because there is no security to verify the sender or receiver.
Most banking accounts are under two-factor authentication, which when gaining access to the SS7 network. Criminals can intercept the code sent to the authentication phone number after they use a phishing attack to steal the victim’s Login credentials and initiate verification code via SMS (Text)
Banks that use 2FA authentication which doesn’t rely on text messages verification won’t be effective in which they authenticate app such as the RSA Token
You may also Like: 11 Security tech terms that you should know.
RSA Secure ID
RSA is one of the first public-key cryptosystems and it’s widely used for secure data transmission. In such a cryptosystem, the encryption key is public and it is different from the decryption key which is kept secret.
How RSA Secure ID Works
When a user attempts to access a protected resource, he is prompted for a unique passcode. The passcode is a combination of their user’s PIN and the code that is displayed on the authenticator token at the time of login.
Some of The Telecom Service Provides Statements
Vodafone spoke person said to Motherboard, “We have specific security measures in place to protect our customers against SS7 vulnerabilities that have been deployed over the last few years, and we have no evidence to suggest that Vodafone customers have been affected.”
Also, they stated that Vodafone working with GSMA, banks and security experts in order to mitigate and protect their customers.
!!DON’T FORGET TO SHARE THIS ARTICLE SO THAT OTHERS CAN BE AWARE!!