Security researchers at Mimecast have recently discovered a new malware campaign, which uses an email method to deliver a weaponize read-only Microsoft Excel spreadsheets to its victims.
LimeRat Malware excuted in Excel Spreadsheet.
T
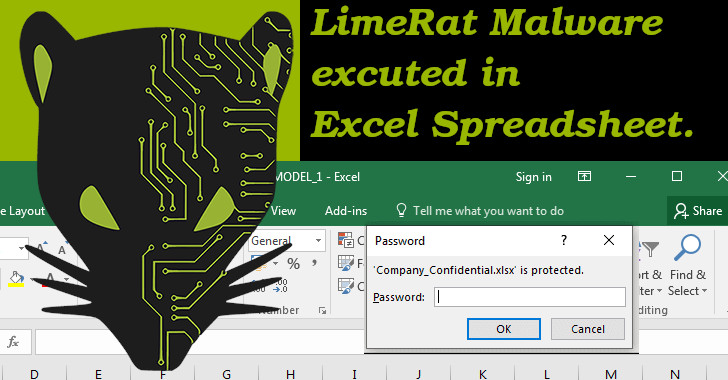
he Microsoft office suits are ship with a wide range of tools for office works, which is one of the most popular tools out there that has been abused continuously by Cyber-Criminals to deliver malware across the planet.At this current moment, attackers are campaign with password-protected excel files, to open the file, the victim is required to enter a password which is in the socially engineered email.
Notorious Hacking Group Launches A New Trojan
For a user to decrypt the password-protected excel file, the victims need to enter the password “VelvetSweatshop ” once the decrypted process has been complete, it onboards malicious macros embedded within start to operate.
After the LimeRAT malware payload loaded, the remote access trojan gives the attacker complete access to its victim’s computer.
“In this specific attack, the cybercriminals also used a blend of other techniques in an attempt to fool anti-malware systems by encrypting the content of the spreadsheet hence hiding the exploit and payload,” researchers told.
The Cyber-criminals behind the malware also can personalize each payload with various attributes. After the Trojan installed and is fully operational swing, it fetches details about the victims such as operating system, CPU, GeoLocation (Country), users, and other information.
The following are the payload capabilities that include Cryptocurrency miner, worm, keystroke logger, screen grabber, information stealer, and ransomware.
The LimeRAT malware is disturbed as an email attachment, social engineering, software ‘Cracks’ and malicious online advertisement ( Malvertising ).
For Windows machines, it was coded in Visual Basic .NET, known for its anti-virus evasion techniques, anti-virtual machine features, small footprint, and encrypted communications.
An exciting feature of the LimeRAT malware is the use of multiple ports for communication, which establishes redundancy for the communication channels. It’s communication with the C&C server encrypted using the AES algorithm.